In one of my previous tutorials we discussed how we can use ardamax key logger to hack remote computers .In this article i will explain What is Realtime spy and i will also explain How you can use Real time spy to hack remote computers

What is Real time Spy ?

Hack a Remote Computer Using Realtime Spy :-
Step 1 :-
First a fall Download Realtime-Spy from Here. After downloading your copy of Realtime-Spy navigate to where you downloaded (in this case it is on the Windows desktop). Double click the Realtime-Spy installer file to start the install.
NOTE: After install is complete you can delete this file!
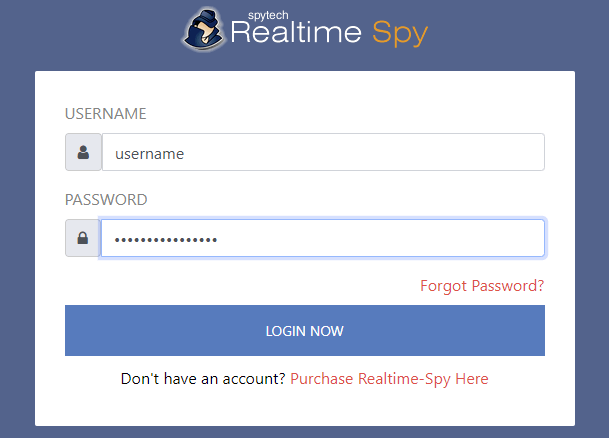
Step 2:-
Upon finishing the installation you will be able to run Realtime-Spy's configuration file immediately. Do this and continue to the next step.
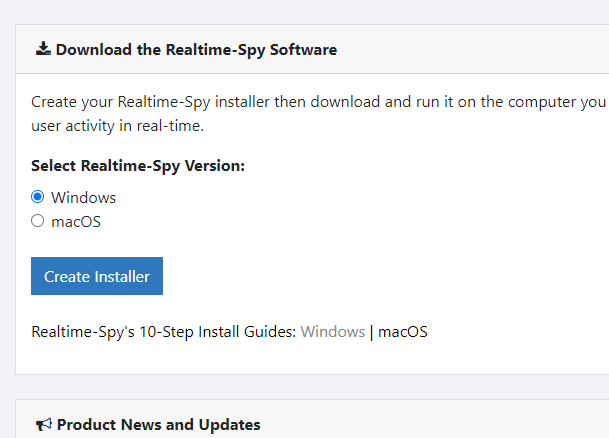
Step 3 :-
You will now see the Realtime-Spy configuration window. Enter in your username and password that you received after purchasing Realtime-Spy. These must be entered EXACTLY as given. They are case sensitive, and take care not to mix up 0's with O's and I's with l's.
After you enter your username and password, choose whether or not you want Realtime-Spy to display a splash warning whenever it is ran, and how often you want it to clear its logs.
After you enter your username/password and select the options you want - press "next" to go to the next configuration panel.
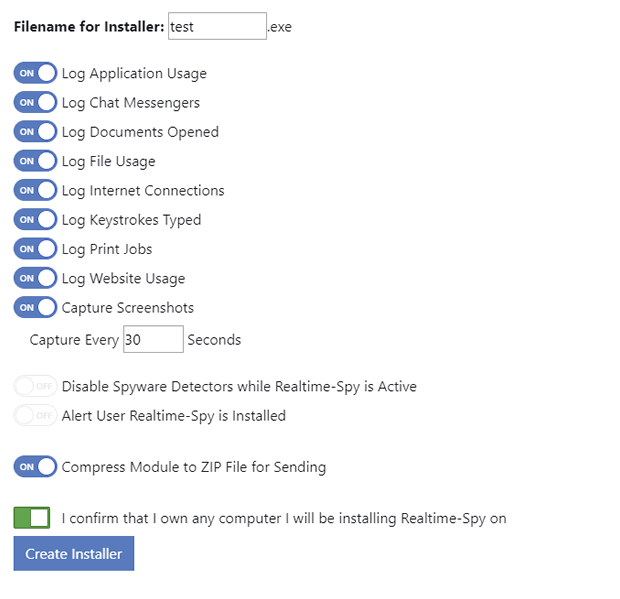
Step 4 :-
When you click "next" Realtime-Spy will verify your settings. If they are correct you will be able to configure your monitoring options, as shown below. Once you have your options set click "create" to create your logging module.
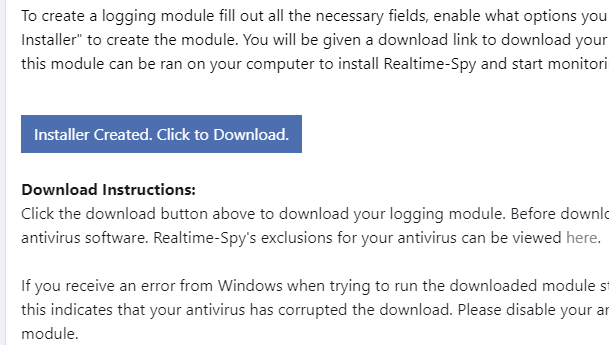
Step 5 :-
Click "create" to create your logging module. You will be prompted for a name to give the file you are creating. In this example we have named it 'test' - you can name it whatever you want. Click Save and you will receive a message similar to the one below.
Remember the location of the file you have just created!
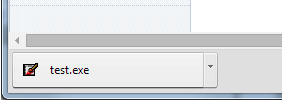
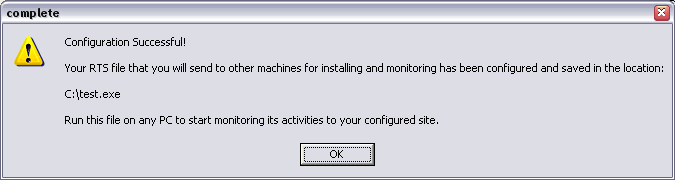
Step 6 :-
Now it is time to send out the file to the remote PC. In this guide we are using Outlook Express on Windows XP.
Click the Create Mail button to open a new mail window.
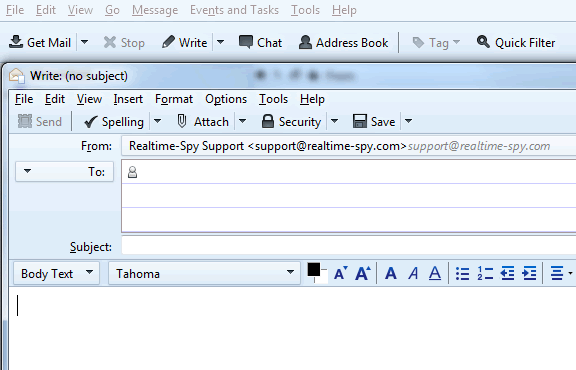
Step 7 :-
Click ATTACH and navigate to where you saved your Realtime-Spy file you created previously. Click on the file and then click 'Attach' to attach the file to your email.
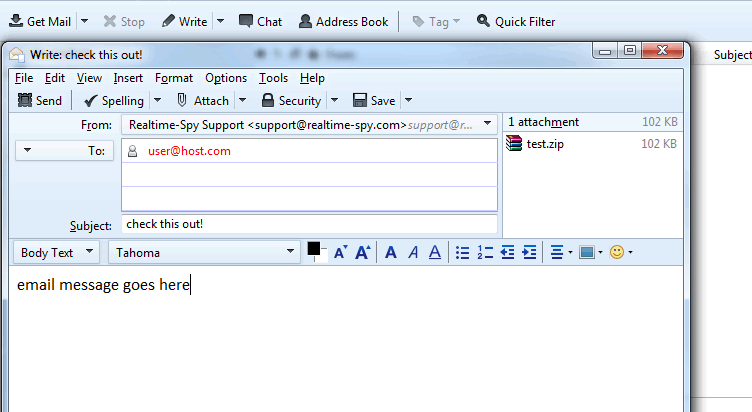
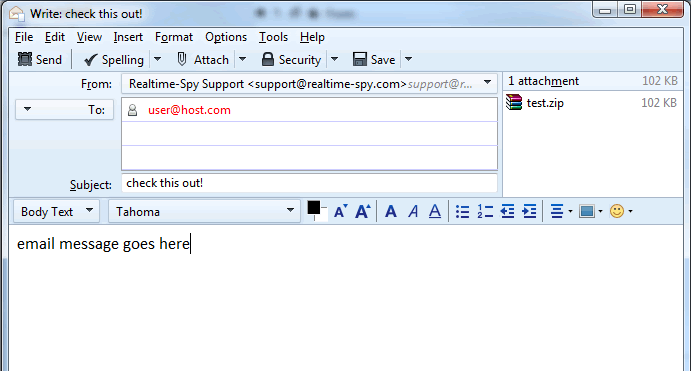
Step 8 :-
You will now have to enter a recipient for the file you are sending, as well as an email subject and body. Notice the size of the Realtime-Spy file - it should be approximately 100-120kb at all times!
Once you are ready to go click Send to send the email!
Step 9 :-
Once you send out the file you can then login to your Realtime-Spy webspace. This is located at www.realtime-spy.com/mems/
Enter in your username/password at the prompt to continue!
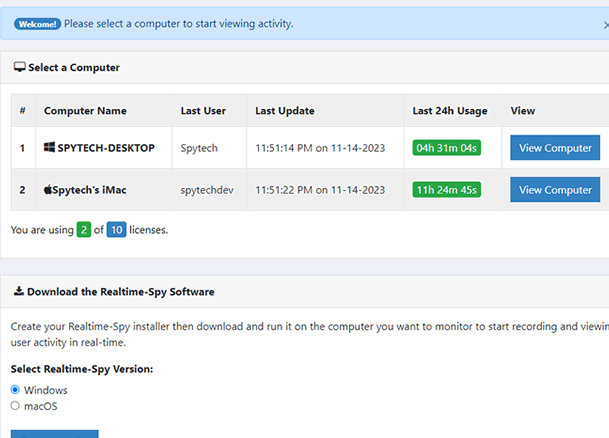
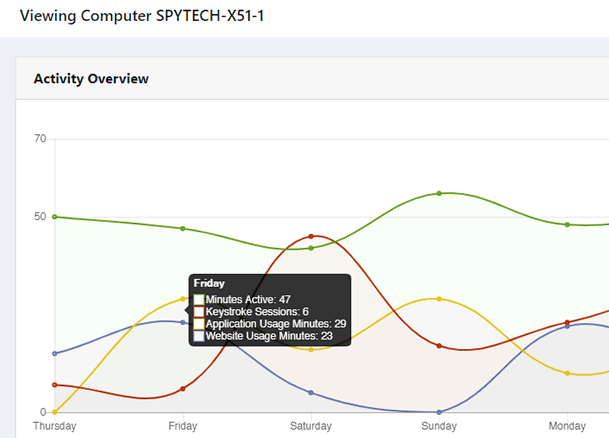
Step 10 :-
You will be presented with your Realtime-Spy webspace. Here you can select and view users that were logged with the file you sent out.
Note: Users will only appear after they have downloaded and executed the file you have sent them.

What is Real time Spy ?
Realtime-Spy is the latest in cutting-edge remote spy software monitoring technology that allows you to monitor ANY PC you own from ANYWHERE. Realtime-Spy is remotely installable .It is one of the best and the Cheapest spying softwares which is out there in the market
Why Realtime spy ?
So now you will ask me, why i should use Realtime spy ? If i can do the same using Ardamax keylogger
for a free of cost .The answer is going to be very simple ,In Ardamax
keylogger there are only few features that you can use to monitor remote
computers , It can be easily found by using Antivirus programs and moreover it needs physical access for instillation

But in Realtime spy no physical installation is needed .It also
has some excellent features like its activity logs are accessible from
anywhere regardless if the remote PC is online or not , Realtime-Spy
logs all keystrokes, websites visited, applications ran, e-mail
activity, chat conversations, screenshots, and many more
Its stealth (i.e) it's totally undetectable by anti viruses.The
best feature i like in Realtime-Spy is it can show you what users are
doing, and typing, in real-time. So overall ardamax keylooger is no
comprision to Realtime-Spy
Hack a Remote Computer Using Realtime Spy :-
Step 1 :-
First a fall Download Realtime-Spy from Here. After downloading your copy of Realtime-Spy navigate to where you downloaded (in this case it is on the Windows desktop). Double click the Realtime-Spy installer file to start the install.
NOTE: After install is complete you can delete this file!

Step 2:-
Upon finishing the installation you will be able to run Realtime-Spy's configuration file immediately. Do this and continue to the next step.

Step 3 :-
You will now see the Realtime-Spy configuration window. Enter in your username and password that you received after purchasing Realtime-Spy. These must be entered EXACTLY as given. They are case sensitive, and take care not to mix up 0's with O's and I's with l's.
After you enter your username and password, choose whether or not you want Realtime-Spy to display a splash warning whenever it is ran, and how often you want it to clear its logs.
After you enter your username/password and select the options you want - press "next" to go to the next configuration panel.

Step 4 :-
When you click "next" Realtime-Spy will verify your settings. If they are correct you will be able to configure your monitoring options, as shown below. Once you have your options set click "create" to create your logging module.

Step 5 :-
Click "create" to create your logging module. You will be prompted for a name to give the file you are creating. In this example we have named it 'test' - you can name it whatever you want. Click Save and you will receive a message similar to the one below.
Remember the location of the file you have just created!


Step 6 :-
Now it is time to send out the file to the remote PC. In this guide we are using Outlook Express on Windows XP.
Click the Create Mail button to open a new mail window.

Step 7 :-
Click ATTACH and navigate to where you saved your Realtime-Spy file you created previously. Click on the file and then click 'Attach' to attach the file to your email.

Step 8 :-
You will now have to enter a recipient for the file you are sending, as well as an email subject and body. Notice the size of the Realtime-Spy file - it should be approximately 100-120kb at all times!
Once you are ready to go click Send to send the email!

Step 9 :-
Once you send out the file you can then login to your Realtime-Spy webspace. This is located at www.realtime-spy.com/mems/
Enter in your username/password at the prompt to continue!

Step 10 :-
You will be presented with your Realtime-Spy webspace. Here you can select and view users that were logged with the file you sent out.
Note: Users will only appear after they have downloaded and executed the file you have sent them.

If you have any doubts regarding the Installation . Please feel free to post a comment




0 comments:
Post a Comment